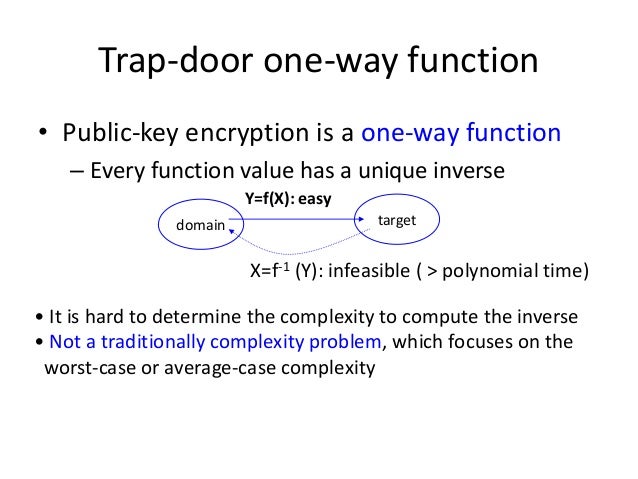
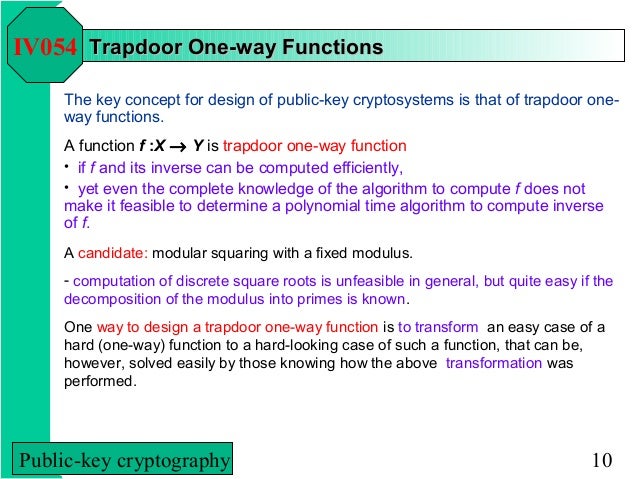
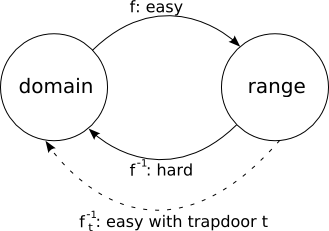
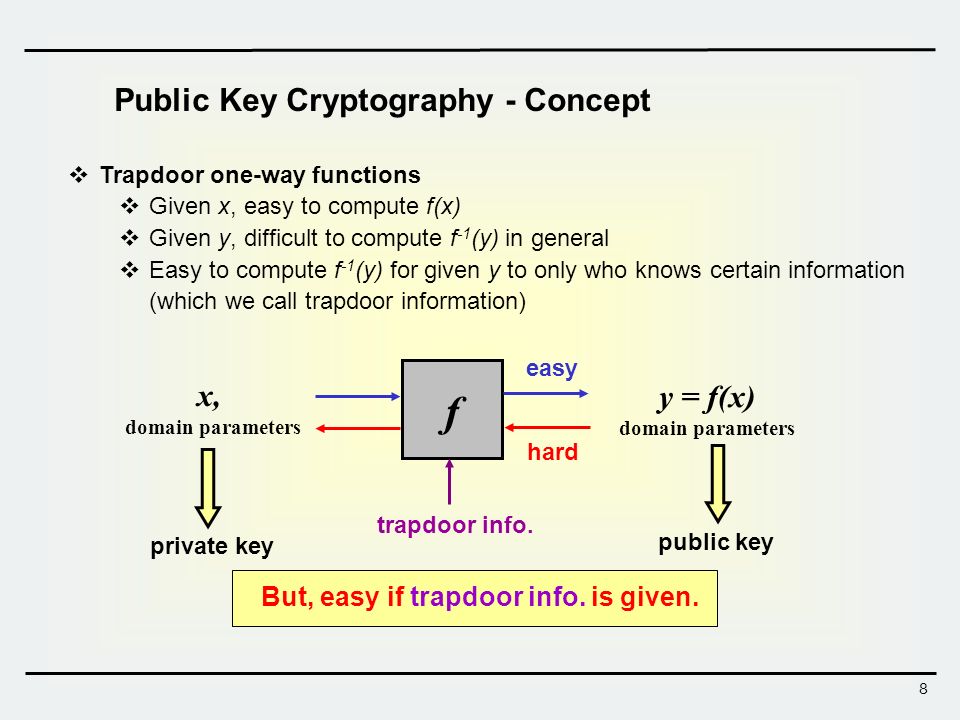
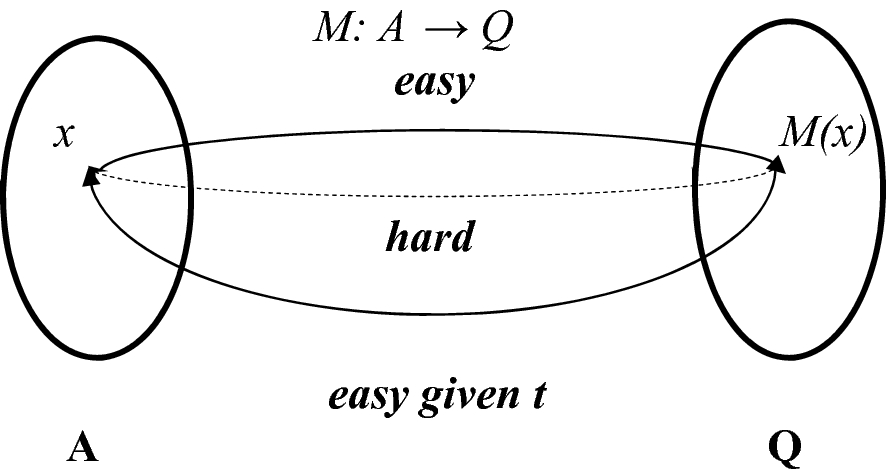
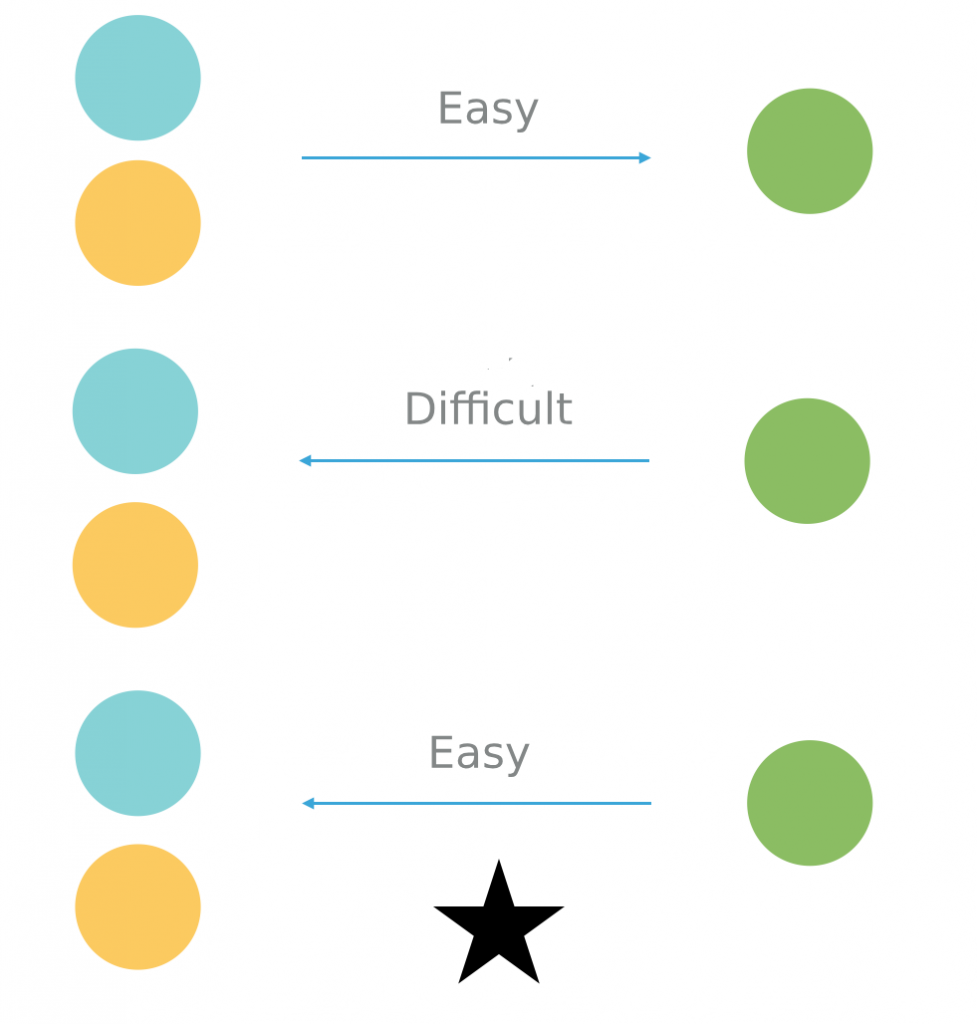
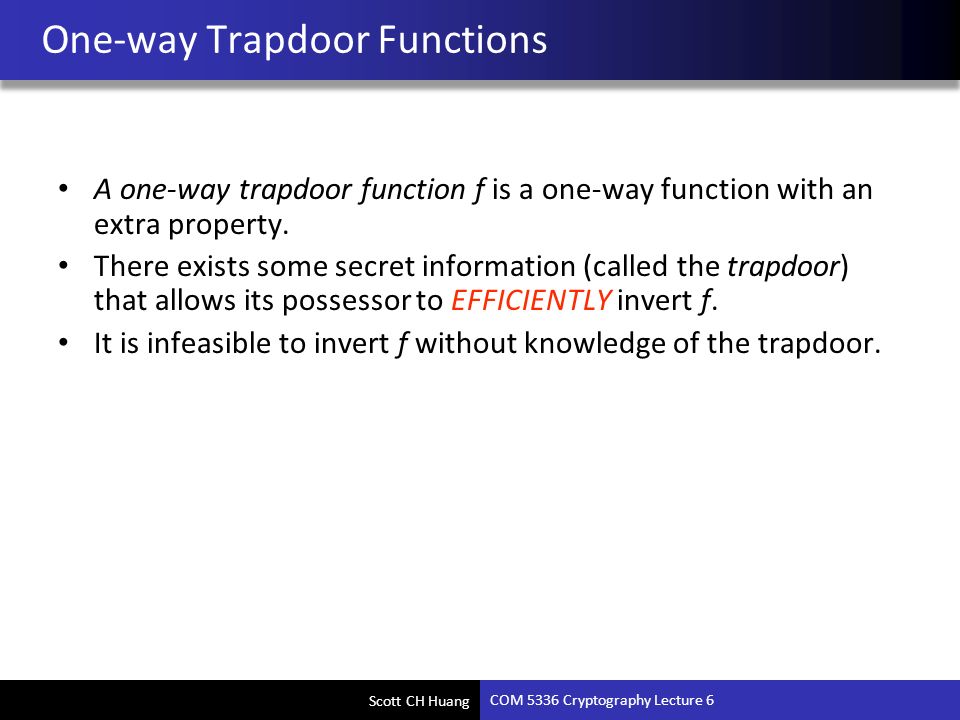
A trapdoor function is a function that is easy to compute in one direction yet believed to be difficult to compute in the opposite direction finding its inverse without special information called the trapdoor.
Trapdoor one way function in cryptography.
Video created by university of colorado system for the course asymmetric cryptography and key management.
In mathematical terms if f.
Since this function was the first combinatorial complete one way function to be demonstrated it is known as the universal one way function.
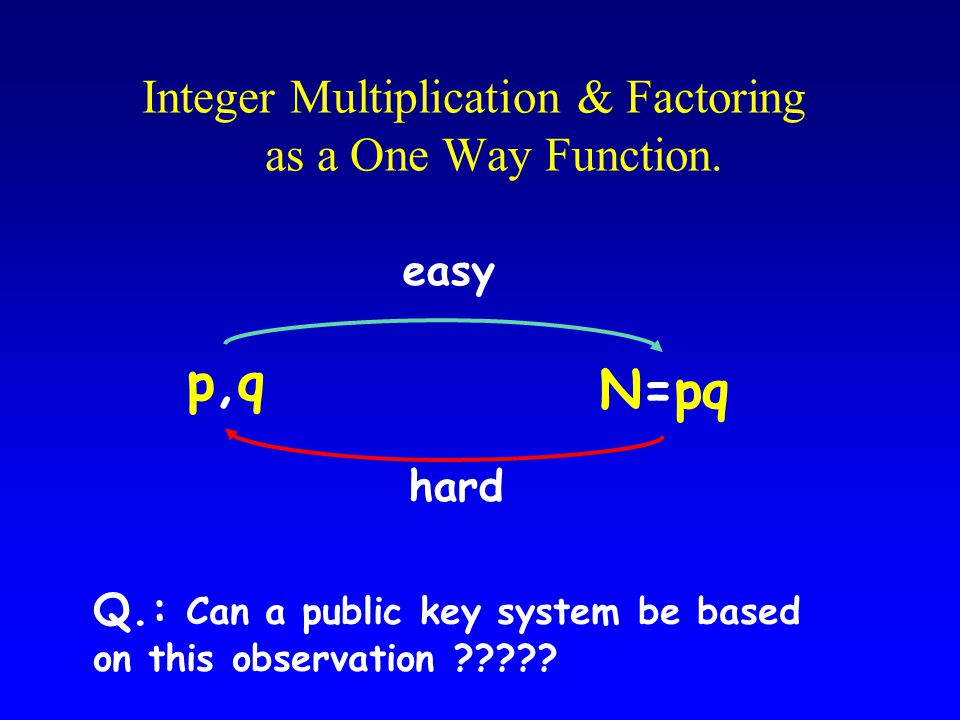
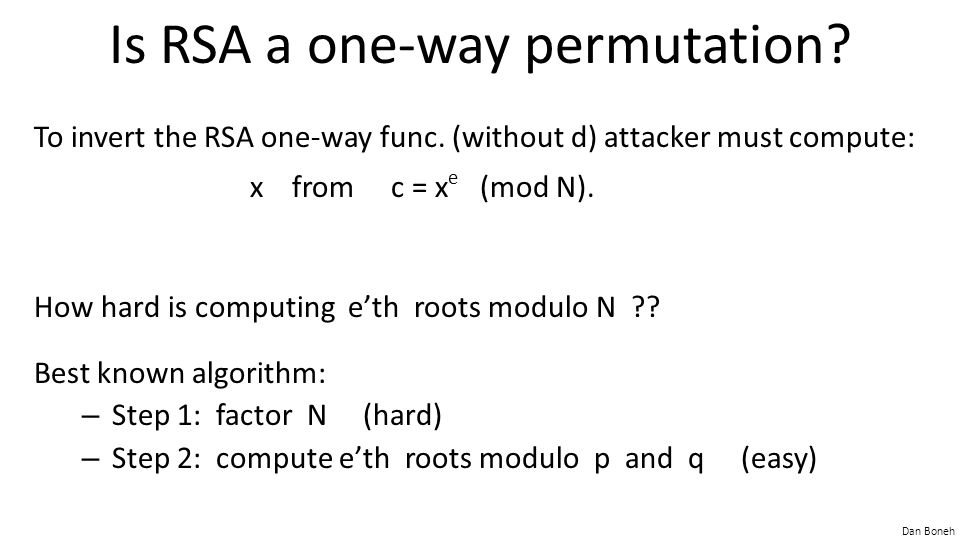
An example of a trapdoor one way function is factorization of a product of two large primes.
However if one has some additional secret information he can easily compute the.
While selecting and verifying two large primes and multiplying them together is easy factoring the resulting product is as far as is known very difficult.
It is not known if a trapdoor one way function can be constructed from any one way function.
As in the case of ordinary one way functions it is easy to compute their values for given data but it is very difficult to compute their inverse functions.
This module reviews the principles and requirements of asymmetric cryptography which uses a pair of keys with one party using a public.
A trapdoor function is a function that is easy to compute in one direction yet difficult to compute in the opposite direction finding its inverse without special information called the trapdoor trapdoor functions are widely used in cryptography.
The problem of finding a one way function is thus reduced to proving that one such function exists.